Recently my brother came to visit and saw our Smart devices in use. They are quite fun to use for everything from background music to lighting control, and my favorite…being used as additional timers in the kitchen.
I received a call a few days after he returned home to let me know that they had purchased their first Smart devices, and wanted to know the best way to ensure that the Internet of Things (IoT) devices are never used as a launch pad into his network. Vigilance is required when implementing IoT devices in your home or workplace. Hackers will exploit any weakness they can detect and with the IoT becoming more prevalent, new holes are being created in your home or work networks.
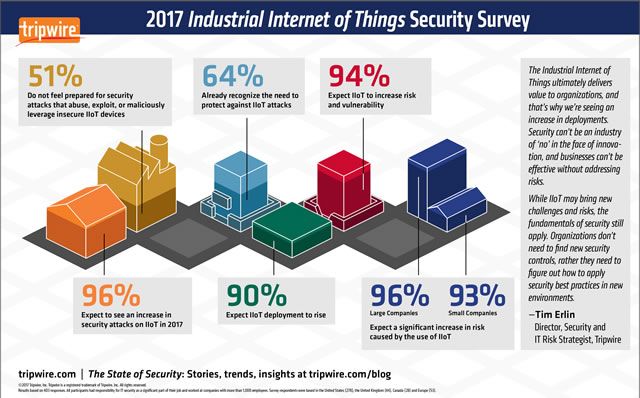
Interest in home-based IoT showed the largest increase in 2016 jumping 12 percentage points from 53 percent to 65 percent. Also, willingness to pay extra for home monitoring services and home control has risen considerably with consumers. Smart bulbs, smart thermostats, smart locks, smart doorbells, smart cams, smart smoke detectors, smart flood sensors, smart vacuums, smart window shades, smart ovens, smart blenders, smart toasters, smart mixing bowls, smart fryers, smart coffee makers, and smart ice makers will all need to be updated. These are no longer simple electronics, they are all tiny little computers with Internet connectivity that will require updates to address security flaws as they are discovered.
It is hard enough keeping up with your desktop, laptop and mobile device. When will you make time to update all the Internet-connected devices in the house to make sure that no one has an open door to your personal information? While it has gotten a bit easier for people to keep computer systems and mobile devices updated, it is much more difficult to monitor these newly connected IoT items.
A smart toaster for example should never be put onto the same network where you do your banking and store family photos. There are many simple solutions to segment these devices from your network. Before you start plugging in devices with abandon, create a plan that separates the traffic, and make sure you stick with it!
The easiest way to protect your data is to segregate your network. Use the guest wireless option on your wireless access point for your IoT devices, and use the primary wireless network for computers, laptops and mobile devices. This will segregate your IoT devices from your network and restrict your IoT devices from being used as a launch pad to probe or attack machines on your network.
When segregating the network, make sure you require the use of a separate set of passwords.
Please note that some wireless access points do not support the capability to deploy more than one network, though this shouldn’t be problem in business-grade Wi-Fi systems. If you don’t have the capabilities to deploy two networks, and don’t want to interrupt your current infrastructure with the replacement of equipment, consider deploying a new network for your IoT devices. This isn’t the cheapest option, but it makes it almost impossible for a device from being used as a launch pad into your network. By adding a couple access points with their own physical wiring directly to your outside Internet connection, your IoT devices are then entirely segregated from your network.
This is not meant to scare you into not using Smart devices. I just suggest that you think about the implications of what is being plugged into your network before blindly installing these IoT devices that are flooding the market.
If you would like help reviewing your plans for Smart device deployment, call Advanced Systems Solutions Inc. and we will help you to ensure that you install devices in the safest manner possible.
Disclaimer: The above information is not intended as technical advice. Additional facts or future developments may affect subjects contained herein. Seek the advice of an IT Professional before acting or relying upon any information in this communiqué.